
WP Engine Ireland is a Great Workplace for Health and Wellbeing

ACF Wins Plugin Madness 2024!

DE{CODE} Strikes a Chord, Achieves Record-Setting Attendance

Elevate Your WooCommerce Store With WP Engine's New Stripe Checkout Integration

WP Engine's DE{CODE} 2024: What’s Next in Modern Web Development

AI, Accessibility, and the Promise of the Universal Web

How WebDevStudios Saves Time and Simplifies Elementor Migrations for Enterprise Clients

Crafted Future: UX For a New Era
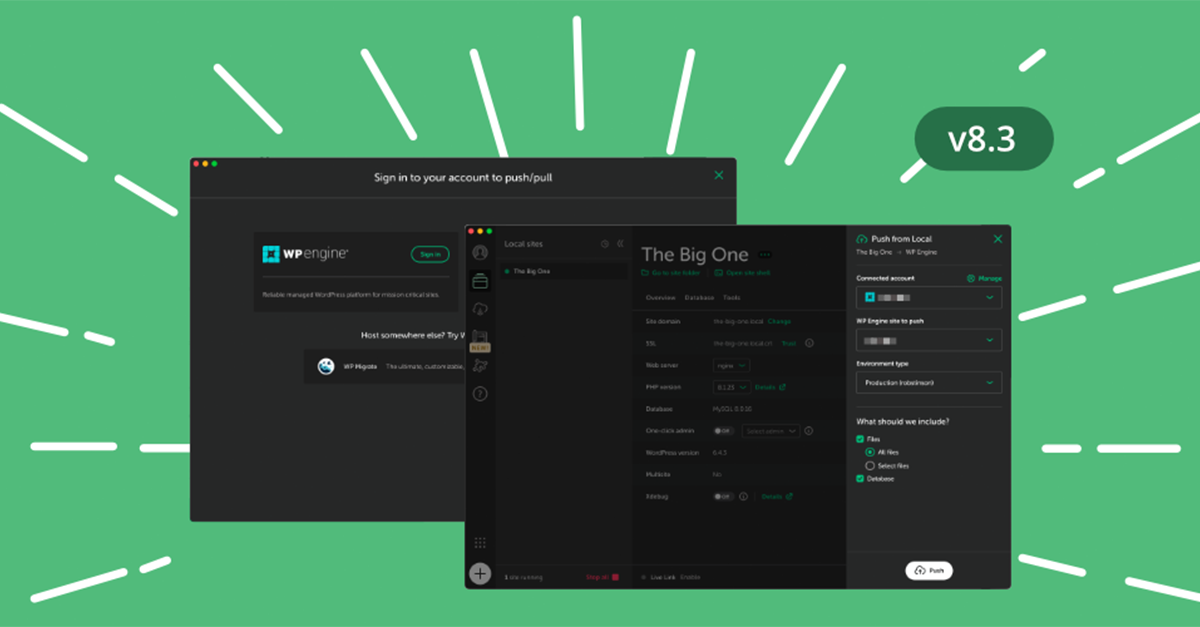
Going From Local to Live Just Got a Whole Lot Easier!

Voting is Open for Plugin Madness!

A Sneak Peek Into DE{CODE} 2024

WP Engine Named a 2024 Best Workplace in Ireland
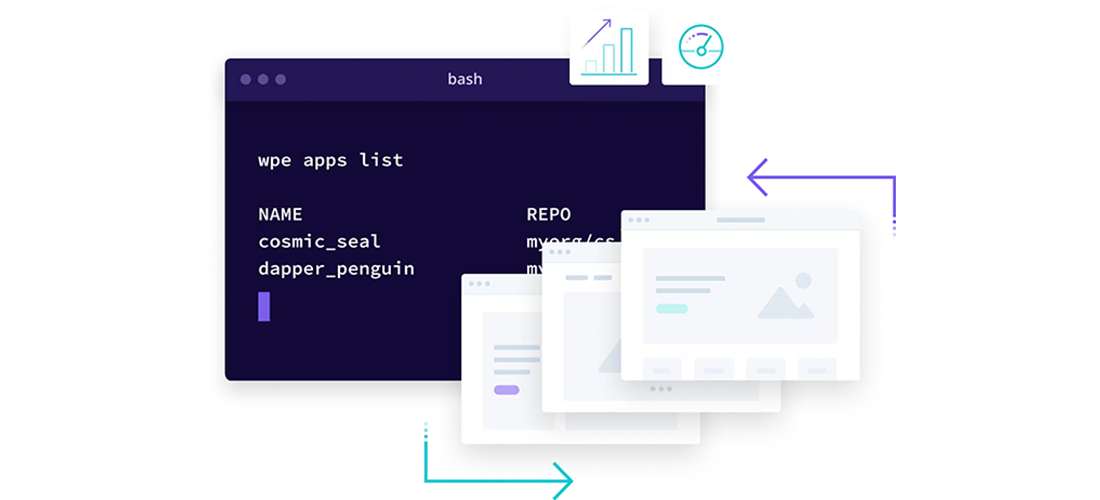
2023 Atlas Year-in-Review

Nominate Your Favorite Plugins for Plugin Madness!

WP Engine Recognized as a Best-in-Class Employer by Gallagher

Celebrating Innovation and Excellence With Art & Science











