
Is Your Site a Security Liability?
Executive summary: The business risk developers can’t afford to ignore
The digital experience is the front door of your online business, and that door is built on WordPress®. The open-source platform is invaluable for its flexibility and speed-to-market. Technical leaders and developers often view self-hosting as a more secure solution for their business-critical, high-traffic digital experiences. WordPress is not inherently less secure than any other CMS, but its ubiquity attracts a higher volume of bad actors.
While WordPress is free to use, the cost of self-managing its security comes at a steep cost. At scale, relying on a pieced-together stack of servers, plugins, and internal developer time can turn a seemingly low-cost solution into a profound and active risk to the entire organization. Your developer team is currently absorbing the cost and complexity of a dedicated Security Operations (SecOps) department—a role they were never hired to fill.
The problem in brief: Self-hosting is a liability
For large or growing organizations, a self-managed WordPress stack is inherently unstable. While you have a great deal of control because you are dealing directly with the servers, the situation is complicated by the need to manage multiple applications and third party vendors. A single, unpatched plugin or a small configuration error can lead directly to regulatory fines, massive downtime, and irreversible reputation damage.
Key takeaways for the developer
This whitepaper serves as an essential guide for the developer to assess and mitigate the true risk of their current setup. The evidence overwhelmingly points to a critical need for a strategic shift:
- The Vulnerability Surface is Exponential: It’s not just the core CMS you must secure. It’s the dozens of third-party plugins, themes, server configurations, network setup, and software that powers the WordPress application that make up your entire stack. Each one is a potential zero-day exploit waiting to happen, multiplying your risk faster than your team can patch it.
- Ad-Hoc Tools Cannot Replace a Systemic Platform: Relying on separate WAFs, scanning tools, and manual patching is reactive and inefficient. A comprehensive, all-in-one solution is necessary to provide peace of mind and protection against increasingly sophisticated cyber threats.
- Vendor Trust Signals: Security frameworks like SOC 2 Type II and ISO 27001:2022 apply to the organization controlling the data and the platform. While WP Engine’s completion of these annual audits does not certify the customer, it serves as a critical vendor trust signal, proving that the hosting partner prioritizes security and mitigates data risks. Achieving and maintaining adherence on a self-managed stack demands massive, continuous organizational resources. The effort to constantly execute, test, and prove security controls across a fragmented system—and continuously adapt to new CMS updates and emerging threats—is an organizational burden that often becomes the root cause of an internal compliance failure.
The developer’s mandate
The developer’s mandate should be to move beyond the time-consuming and reactive approach of patching and instead focus on eliminating the liability altogether. This guide provides the framework you need to quantify the risk, calculate the true Total Cost of Ownership (TCO) of your current approach, and build a definitive business case for a secure, expert-managed platform. The future of your digital experience depends on it.
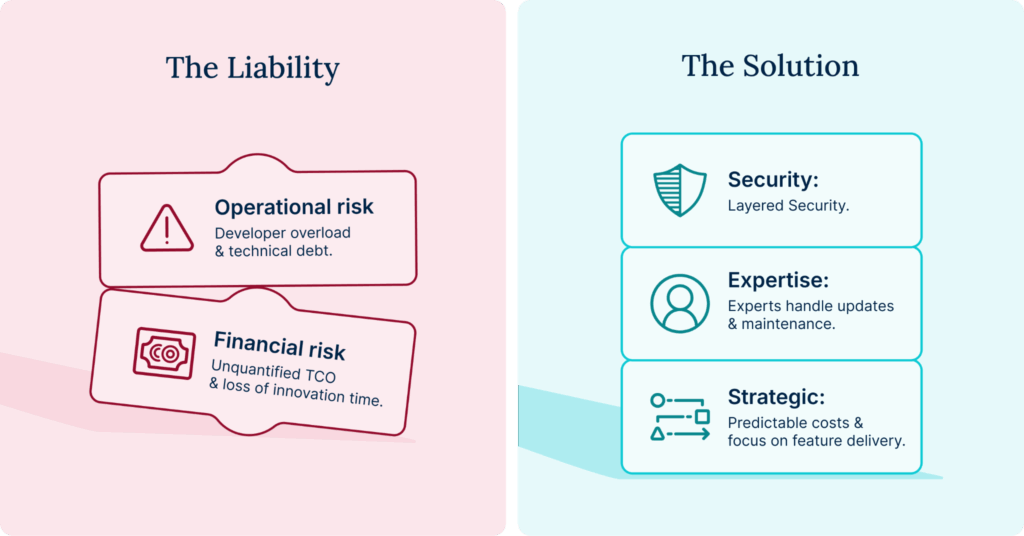
Introduction: The unseen cost of self-hosted security
For the technical leader—the VP of IT, the Tech Lead, or the Developer responsible for the integrity of the corporate digital experience—the primary mission is clear: innovation and uptime. Your focus is on time-to-market, scaling new campaigns, and leveraging the flexibility of open source to deliver features that drive business growth.
But there is a harsh truth that often overrides innovation: security is the absolute foundation. Without a bulletproof security posture, every new feature you deploy simply increases your organization’s exposure.
The developer’s dilemma: Security by necessity, not specialization
WordPress powers over 40% of the internet, and for good reason. It’s powerful, flexible, and fast to deploy. Yet, this flexibility has created an insidious expectation for IT teams: that security for a high-value, high-traffic asset can be handled in addition to their primary development and maintenance duties.
This is the core dilemma for the developer and IT roles: you are tasked with implementing security measures, but you rarely have the resources, training, or specialized mandate of a dedicated SecOps team.
You are not just writing code. You are constantly managing:
- Patching schedules for core, themes, and dozens of plugins.
- Server and operating system configurations.
- Manual Web Application Firewall (WAF) rule tuning.
- Evolving threats that place strain on a dev team forced into a SecOps role.
This quickly results in technical overload. It creates a permanent state of triage, forcing your team to prioritize the tyranny of the urgent (fixing daily issues) over the long-term strategic work of innovation and risk mitigation.
Self-hosting: The stack of vulnerabilities
The term “self-hosted WordPress” sounds simple. It might actually be simple, if the site itself is small and doesn’t get much traffic. For larger, more complex, or scaling WordPress sites, it instead describes a massive, pieced-together system where you inherit 100% of the security burden. This complexity is the fundamental root of your risk.
The security environment of a self-hosted WordPress site has multiple pieces. Managing them is a time-intensive process that uses up resources that could instead be spent on innovation.
- The Core CMS: Its open-source nature means vulnerabilities are frequently discovered and publicly disclosed.
- The Server/Cloud Layer: Your AWS, Azure, Digital Ocean, etc. setup, including network policies, load balancers, and operating system updates.
- Themes and Plugins: Dozens of unvetted, third-party code packages, each with its own potential security flaws and patching schedule.
- The Developer Workflow: The git repos, staging environments, and deployment pipelines, all of which must be secured end-to-end.
- CDN/Edge Layer: External network services like Cloudflare or Akamai, where Web Application Firewall (WAF) and DDoS rules are set up to protect the site before visitors ever reach the origin server.
When one link in this chain fails, the integrity of the entire business is compromised. The perceived low cost of a self-hosted setup becomes a dangerous fallacy when weighed against this systemic risk.
Elevating the risk: From technical bug to business liability
A security breach on a WordPress site can rapidly escalate into a catastrophic risk for your business. The consequences are immediate and far-reaching. For instance, a breach of customer data via a vulnerable database or form handler can trigger massive financial penalties under standards like GDPR, CCPA, or HIPAA.
Beyond regulatory consequences, the downtime, defacement, or public disclosure of a data breach erodes customer trust and can halt critical digital marketing and sales initiatives for months, causing significant reputational damage. Furthermore, every hour and dollar spent on forensic recovery and remediation is time and capital that cannot be spent on building new, revenue-driving features, ultimately resulting in halted growth.
The goal of this whitepaper is to move beyond mere patching; it is to equip you, the developer, with the authoritative framework needed to assess the true liability of your self-hosted environment and justify a move to a more secure, compliant, and sustainable platform solution.
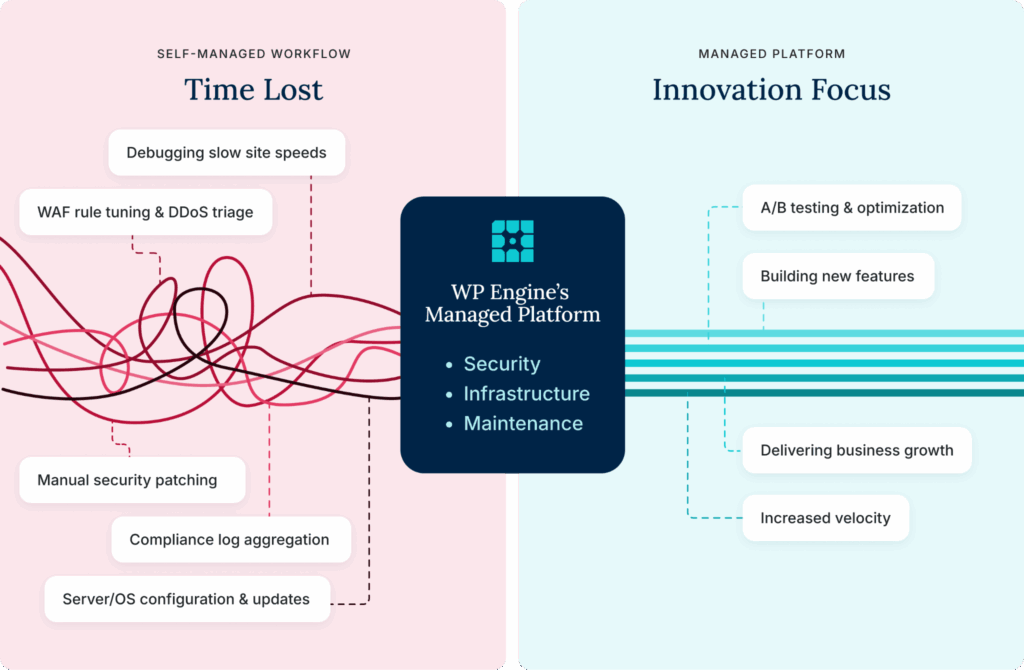
The anatomy of a self-hosted WordPress security flaw
The power of WordPress lies in its open-source flexibility, but that freedom comes at a cost. For developers managing a scaling digital experience, this open ecosystem creates an exponentially complex security challenge.
When you choose to self-host, you aren’t just managing the core CMS. Instead, you are personally inheriting 100% of the risk from the entire technology stack. Your environment transforms from a simple website into a sprawling attack surface where one small flaw in any component can lead to a catastrophic breach.
The expanding attack surface
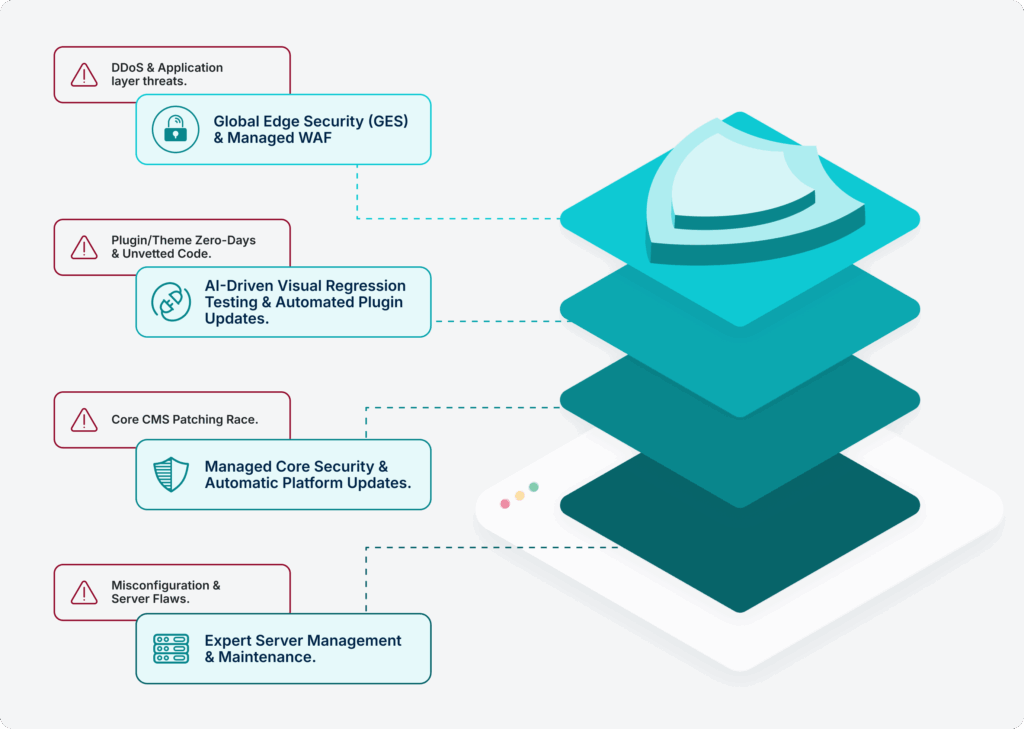
Security is only as strong as its weakest point. For a self-hosted WordPress site, this weakness is multiplied across four primary layers you are directly responsible for managing.
- The Core CMS: WordPress is the world’s most popular CMS, making it the top target for attackers. New Common Vulnerabilities and Exposures (CVEs) are discovered regularly. Your team is in a constant, reactive race to test, stage, and deploy patches to multiple environments before a known vulnerability can be exploited in the wild.
- Plugins and Themes: This is the single largest security headache for any developer. You may have dozens of third-party components installed—possibly from unvetted sources—each introducing potential flaws. It is an impossible task to manually vet the code quality, update frequency, and security commitment of every single plugin and theme your site relies on. If just one popular component is abandoned or suffers a flaw, your security integrity is compromised instantly.
- Authentication and Brute Force: As sites scale and their value increases, they become targets for automated brute force attacks. While self-managed tools can mitigate some attempts, managing the configuration, monitoring, and scaling of robust authentication protocols (like two-factor authentication) and blocking malicious IPs across a globally distributed site network is a significant drain on developer resources.
- Misconfiguration at the Server Layer: The underlying hosting environment is often the source of risk. The responsibility to correctly configure PHP versions, database permissions, web server settings (Apache/Nginx), and the operating system often falls to the developer. An incorrect .htaccess rule or an outdated PHP module is not a WordPress bug—it’s a self-hosting configuration risk that can open the door to unauthorized access.
- The Edge/CDN Layer: This includes external services like Cloudflare, Akamai, or Fastly, where the WAF and DDoS rules are configured. Managing the rules, performance, and security of a third-party CDN adds a complex, critical layer of manual maintenance that must be constantly monitored and tuned to protect the site before visitors ever reach the origin server.
| Security Risks | The Burden of Self-Hosting | WP Engine’s Platform Solution |
| Plugin and Theme Bloat | Manually vetting and updating 50+ third-party components is an impossible task that creates the largest entry point for exploits. | The WP Engine platform offers Smart Plugin Manager (SPM), which automates plugin updates and uses visual regression testing to ensure updated plugins don’t break your site or change its appearance. |
| Zero-Day Vulnerabilities & Core CMS | Your team is in a constant, reactive race to test, stage, and deploy patches, which creates a significant time-to-patch gap. | WP Engine manages automatic WordPress updates and maintenance , including managed upgrades to WordPress core to ensure your site is secure. Server operating systems and software are also updated on your behalf. |
| Authentication and Brute Force | Scaling sites are targeted for automated brute force attacks. Manual tools and configurations are often insufficient to manage the volume and complexity. | WP Engine offers SSO out of the box ready for implementation, and in tandem with our Seamless Login, it provides a fully secure path to wp-admin. By default, Multi-Factor Authentication (MFA) is forced for all users. Additionally, WP Engine’s proprietary firewall blocks brute force attacks and prevents enumeration (stopping bots from scraping for author ID information). |
| Misconfiguration at the Server Layer | Security gaps in PHP versions, database settings, and server OS configurations are manual risks that fall entirely to the developer. | WP Engine’s experts handle server management, including configuration, server maintenance, databases, and data centers, taking that task off your plate with confidence. |
| WAF/DDoS Configuration and Management Overload | Manually configuring, tuning, and monitoring complex WAF rules and DDoS mitigation on external CDN services, which requires constant attention from specialized personnel. | In addition to its advanced network, WP Engine offers Global Edge Security (GES) with a managed WAF to detect and filter out malicious acts at the network edge. It includes advanced DDoS Attack Protection that can detect and drop volumetric attacks, as well as blocking common vulnerabilities like XSS, SQL injections, and other application layer threats. |
Advanced attack vectors
Beyond the common flaws created by unmanaged components, WordPress sites must contend with increasingly sophisticated attacks that target the data and infrastructure directly.
- Cross-Site Scripting (XSS) and SQL Injection (SQLi): These attacks exploit insufficient input validation within third-party themes or custom code, allowing attackers to inject malicious scripts or manipulate your database. For an eCommerce or lead generation site, this can lead to the direct theft of customer personally identifiable information or sensitive corporate data.
- Zero-Day Vulnerabilities: The Time-to-Patch Gap: The most dangerous vulnerability is a zero-day vulnerability, a flaw that is discovered and exploited before the component vendor or your team has a fix. In a self-hosted environment, your team’s reaction time is the only thing standing between a security flaw and a business breach. This gap between the exploit and your manual deployment process is the moment of maximum risk.
The net effect of this complexity is technical overload, forcing your talented developers into perpetual maintenance and triage instead of strategic innovation. This constant fire-fighting mindset is the greatest security risk of all.
The compliance conundrum: When ‘good enough’ isn’t
For a growing organization, security is not just a technical checklist; it is a legal and business mandate. The demands of modern digital governance, driven by international data privacy laws and stringent industry standards, have created a compliance chasm that self-managed WordPress sites are ill-equipped to bridge.
For the developer, this means shifting the perspective from “How do I prevent a hack?” to “How do I provide auditable proof to a regulator or internal legal team that a hack can be mitigated?”
Security as a legal mandate: Compliance is foundational
In the enterprise context, compliance failures are no longer technical oversights; they are board-level risks. A failure to adhere to global privacy regulations or security frameworks can lead to massive fines, mandated operational halts, and long-term erosion of investor and customer trust.
Crucially, compliance cannot be added later. It must be engineered into the organizational layers of the business itself.
Navigating the compliance checklist
When selecting a hosting vendor, your organization assumes the risk associated with that vendor’s security posture. The onus of proof is on you to demonstrate that your organization adheres to recognized security and availability standards. For an organization self-hosting, this means dealing with a massive administrative burden, as you must constantly implement, test, and audit security for the infrastructure you control.
Choosing a vendor that meets frameworks like SOC 2 and ISO 27001 is a critical step in mitigating supply chain data risk and demonstrates organizational rigor in vendor vetting.
- SOC 2 Type II: This is the gold standard for service organizations managing customer data. WP Engine’s successful completion of this audit signifies that we prioritize security and availability, reducing your internal vendor risk burden. A developer running a server on a public cloud must independently implement and prove compliance across patching, access control, disaster recovery, and change management—a task that requires a full-time, specialized Governance, Risk, and Compliance (GRC) team.
- ISO 27001:2022 The global standard for managing information security. When a vendor is certified under this standard, like WP Engine is, it ensures you are dealing with a partner that adheres to world-class security management protocols. Without a certified partner, this is a monumental internal project for your team, involving defining scope, establishing policies, managing assets, and conducting internal audits.
- GDPR, CCPA, and Data Residency: Data privacy laws mandate where customer data is stored, how it is logged, and how access is controlled. If a self-hosted vulnerability exposes personally identifiable information via a vulnerable database or unmanaged form plugin, your company faces direct regulatory action. Choosing a specialized partner provides the confidence that the platform itself is built for regional data residency and compliance logging. However, it should be noted that no matter what platform you are on, you are primarily responsible for ensuring the privacy of your user and customer data.
The true cost of self-hosted security: Time, tools, and talent
The perception that self-hosting on a public cloud is the “cheapest” way to run enterprise WordPress is a dangerous myth. When you move beyond the server rental fee and factor in the actual resource expenditure the total cost of ownership skyrockets, transforming perceived savings into a debilitating, recurring business expense.
The TCO fallacy
The TCO of your self-hosted setup extends far beyond the monthly cloud bill. It includes critical, often-ignored factors that directly erode profitability and innovation bandwidth.
- Developer Time as a Security Cost: You hired your senior developers for innovation and feature delivery. When they’re spending 10 to 15 hours per week manually patching, triaging security tickets, and configuring WAF rules, that time is lost to your product roadmap. This technical overload means your highest-paid employees are performing essential but automatable operational tasks.
- The Cost of Talent Retention: The constant pressure of managing security for an unstable, self-hosted stack leads to burnout. Developers prefer to innovate, not to fight fires. The cost of replacing a high-value developer due to burnout far outweighs the cost of a managed platform solution.
- The Unquantifiable Cost of Opportunity: The ultimate hidden cost is the opportunity lost. Every hour spent on security maintenance is an hour not spent building a new customer-facing feature, optimizing the conversion funnel, or exploring new markets.
The limitations of self-managed security tools
In a self-hosted environment, developers are forced to piece together a security solution from disparate, often reactive tools. This patchwork approach creates gaps in coverage and demands constant, specialized management that few internal IT teams can sustain.
- Firewalls and WAFs: While a standalone WAF can block basic attacks, it requires continuous tuning to protect against zero-day and sophisticated, application-level exploits common in the WordPress ecosystem. Developers are typically left to manage complex rule sets manually, leading to either an overly permissive firewall that lets threats through or an overly aggressive one that blocks legitimate traffic.
- Malware Scanning and Remediation: Self-managed malware scanners are often reactive, flagging infections after they have already occurred. Remediation is time consuming and expensive, involving manual code cleanup, deep forensic analysis, and ensuring backdoors are eliminated. An integrated platform prevents infection at the source, rather than asking the developer to clean up the mess afterward.
- The Patching Paradox: Security requires proactive, immediate action. A security flaw is announced, and your developers must then manually execute a workflow: download the patch, test it across staging environments, and deploy it across all production sites. This inevitable delay between vulnerability announcement and manual deployment is the time-to-patch gap, and it is the window of maximum risk for your site.
Technical debt as security debt
When time is short, security tasks are inevitably deferred. Every deferred patch, every unoptimized server configuration, and every unvetted plugin becomes a form of technical debt.
In the context of security, this technical debt accumulates exponentially. What starts as a minor delay in applying an update can become the entry point for an attack that costs the business millions. The developer’s team is forced into a reactive cycle, constantly chasing mounting complexity and security debt, rather than investing in strategic, future-proof stability.
The true solution is to remove the underlying burden by shifting the responsibility for platform security to a provider whose core business is to eliminate this liability.
Conclusion: Moving from liability to strategic asset
The evidence presented throughout this guide leads to one inescapable conclusion: for large businesses or those poised to grow, the self-managed security model for WordPress is fundamentally broken. It is a system built on outdated assumptions that places a disproportionate burden of risk management and compliance onto developers who are already facing technical overload.
The choice is clear. You can continue to manage the liability, perpetually fighting the technical debt, zero-day vulnerabilities, and lost developer time inherent in a self-hosted stack, or you can choose to eliminate that liability entirely.
Shifting the security paradigm
Moving from liability to strategic asset requires a fundamental shift in how your organization views its digital experience platform. This is not about choosing a different server; it is about choosing a different security model.
When you partner with a platform that is purpose-built for enterprise WordPress, you shift responsibility for the foundational security and compliance layers to a team of experts whose sole focus is protecting and optimizing your site. This transition immediately achieves three critical goals for the developer:
- Eliminate the Attack Surface Burden: You offload the constant, draining task of patching core, plugins, and server configurations. The platform automatically handles proactive defense, WAF tuning, and vulnerability remediation across the entire stack.
- Auditable Compliance: You gain immediate access to an infrastructure that is already built, audited, and maintained to the highest global standards, providing the audit-ready logs and proof of control your GRC and legal teams require.
- Reclaim Developer Bandwidth: Your most valuable talent is freed from the endless, reactive cycle of security maintenance and fire-fighting. Their time is re-invested into innovation, feature development, and delivering the business growth your leadership demands.
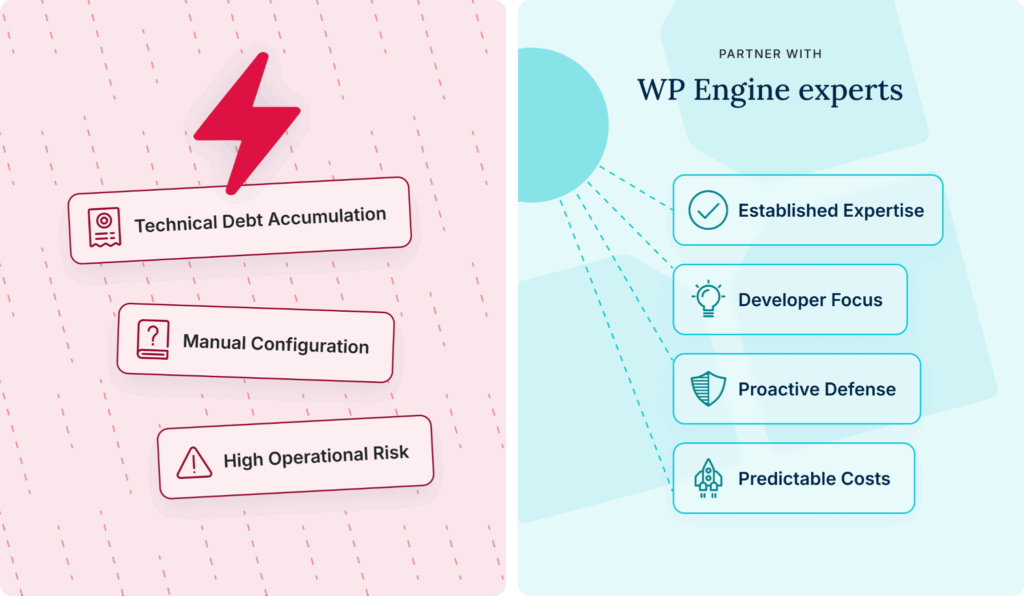
Your Mandate: Justify the Strategic Shift
As the developer responsible for the integrity of your digital experiences, your role is to initiate this strategic change. This is not just a technical recommendation; it is a business justification to move from a costly, unsustainable reactive model to a scalable, proactive growth engine.
The question shouldn’t be whether you can afford to invest in enterprise-grade security, but whether you can afford the often devastating cost and security of continuing to manage it yourself.
Don’t just patch your sites; transform your security posture by moving to a secure, compliant platform. Contact us to discuss how WP Engine can help you take the steps to a secure, enterprise-grade digital experience.
