
Understanding Upcoming Changes to Let’s Encrypt’s Chain of Trust
At WP Engine, we’re committed to ensuring your websites are always secure and easy to access. To this end, we use Let’s Encrypt SSL Certificates to safeguard the communication between your site and its visitors, providing peace of mind that your digital presence is well-protected.
Let’s Encrypt remains a leader in SSL protection, providing SSL certificates to more than 260 million websites worldwide. However, we wanted you to be aware of significant changes coming to its chain of trust hierarchy, which could impact older devices and operating systems.
The impacts of these changes are expected to be minimal, but understanding how they might affect your site is important for maintaining uninterrupted service and trust with your site users.
Read on for a quick breakdown of what you need to know.
What’s a chain of trust?
A chain of trust is a fundamental concept in cybersecurity that ensures each component in a system—whether it’s hardware or software—can be trusted.
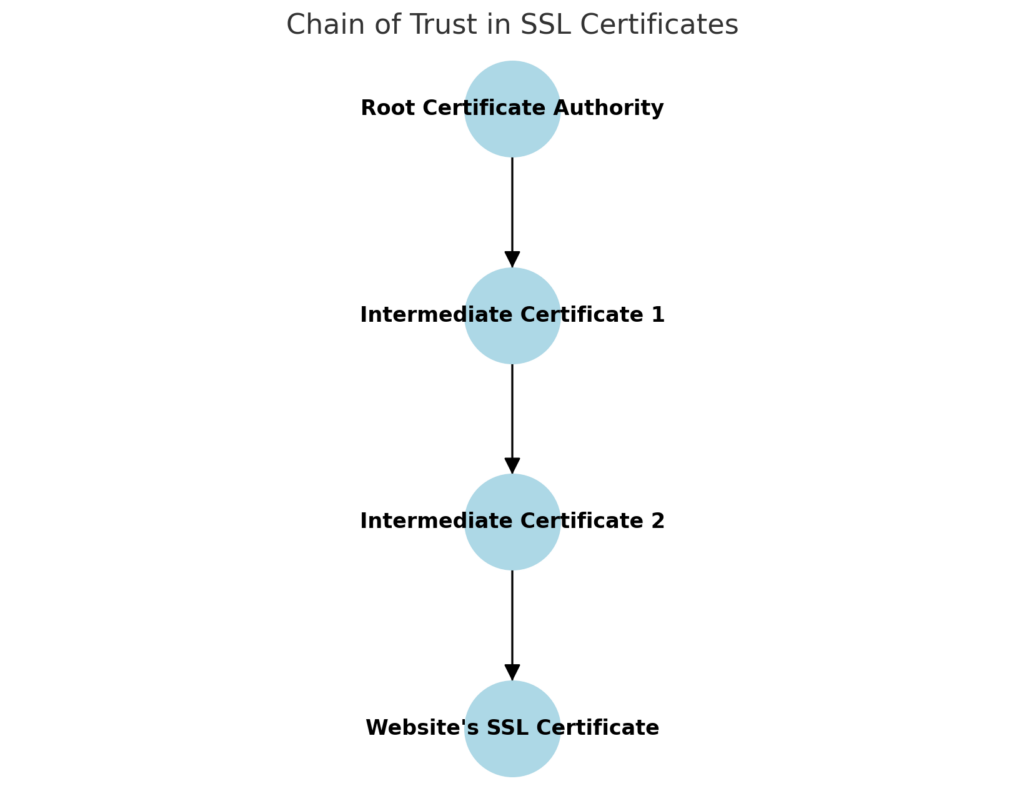
In relation to SSL/TLS certificates, the chain of trust starts with a trusted root certificate authority (CA) at the top and extends through intermediate certificates down to the SSL certificate installed on your site.
Each certificate in the chain is verified by the one above it, creating a secure link back to the trusted root. This process ensures the SSL certificate used by your site is authentic and can be trusted by users’ browsers and devices.
In some cases, particularly when a new CA is introduced, its root certificate might not yet be widely trusted by older devices and systems. To address this, a cross-signing method can be used, where an established CA vouches for the new CA by signing its certificate.
This creates an additional link in the chain of trust, allowing older devices to recognize and trust the new CA’s certificates. Cross-signing was particularly useful in the years following Let’s Encrypt’s launch, as it ensured older Android devices could trust its certificates, preventing disruption for those users.
Over time, this approach helped increase the percentage of Android devices capable of natively trusting Let’s Encrypt’s certificates from around 60% to over 93%, significantly reducing the need for cross-signing as newer devices became compliant.
What’s changing with Let’s Encrypt’s chain of trust?
In June 2024, Let’s Encrypt announced it was discontinuing access to its cross-signed chain, in preparation for the expiration of its cross-signed certificate, on September 30, 2024.
Both have long extended Let’s Encrypt’s chain of trust to older devices and operating systems that rely on legacy methods to validate SSL certificates. However, the need for cross-signing has diminished in recent years, especially as the percentage of compliant Android devices (capable of natively trusting Let’s Encrypt’s ISRG Root X1 certificate) has risen to over 93%.
The remaining 7% represent unpatched, often unsafe Android devices, and Let’s Encrypt’s decision to shorten the chain of trust is indeed aimed at enhancing privacy and security. By phasing out the cross-signed chain, Let’s Encrypt aims to streamline the trust process, reducing potential vulnerabilities associated with maintaining support for outdated systems.
While this update will improve efficiency and security for most users, it could result in some older, unpatched devices no longer recognizing Let’s Encrypt certificates, leading to potential access issues.
For the vast majority of users on modern devices, the impact will be negligible. However, it’s important to assess whether your audience includes users on older devices and, if so, to consider potential mitigation strategies.
This is because these older systems may no longer recognize the certificates issued by Let’s Encrypt without the cross-signed chain, leading to potential security warnings or blocked access.
Again, the effects of this change will be negligible for most websites. However, it’s important to assess whether your audience includes users who may be on older devices and, if so, what potential mitigation strategies might be.
How exactly will it impact my users?
Every browser and operating system relies on a certificate trust store to verify the authenticity of SSL/TLS certificates presented by websites. This trust store contains a list of trusted certificate authorities (CAs), including Let’s Encrypt, that browsers and other devices use to validate a website’s security.
When a CA like Let’s Encrypt updates its trust model, devices with outdated or unsupported operating systems may lose their ability to recognize and trust certificates issued by that CA, leading to potential security warnings or blocked access.

For example, Android devices running versions below 7.1.1 are particularly at risk (the current version of Android is 14, and Android 7 reached end-of-security-support in October 2019).
Let’s Encrypt estimates that around 6% of Android devices will be affected by this change, which could result in users encountering security warnings, being unable to establish a secure connection, or even being blocked from accessing your site.
The impact on your users will largely depend on the composition of your audience. That said, it’s important to monitor your website access logs to identify the devices your site visitors are using. Specifically, you should look for Android user-agents running version 7 or earlier, such as: ‘Linux; Android 7.0.'”
How can I prepare for potential impacts?
Being proactive in addressing these issues can help ensure all site users, regardless of their devices, continue to have a secure and seamless experience on your site.
Additionally, you may want to communicate with your users, particularly if you know a portion of your audience uses older devices, to inform them of the upcoming changes and even suggest they update their operating systems or browsers to avoid potential access issues.
For customers concerned about a wider impact, working with a third-party CA, such as SSL.com may be of interest. WP Engine offers the option to import a third-party SSL certificate, however, there are some additional requirements and stipulations to consider.
More importantly, many third-party CAs may have also curtailed support for older devices, so customers should verify the following if they choose to pursue this route:
- The CA currently supports older devices and plans to maintain this support
- The CA is compatible with WP Engine
You can find more information about third-party CA’s here, as well as additional workarounds for extending Android Device compatibility here.
Providing you with confidence online
As technology advances, so do the challenges and opportunities that come with securing your digital presence. That’s why we offer a range of resources and tools designed to help you stay ahead of the curve.
From securing your site with SSL certificates to providing advanced security and performance solutions, we’re dedicated to providing you with confidence online. Visit wpengine.com or speak with a representative now to find out more.
Start the conversation.