Global Edge Security (GES)
Global Edge Security (GES) is an enterprise-grade performance and security product extension that can be purchased for any WP Engine hosting plan. With GES you will receive several features powered by Cloudflare: managed Web Application Firewall (WAF), advanced DDOS Mitigation, Cloudflare CDN, and automatic SSL Installation.
Not sure what the differences between GES and our other network types are? Check out our network comparison guide.
Global Edge Security can be purchased as a product extension for Shared plans from the Modify Plan page. Premium plans can purchase GES as a product extension by speaking with their Account Manager or the WP Engine Sales team. GES is included with Secure Hosting plans. Learn more about purchasing product extensions.
Managed Web Application Firewall (WAF)
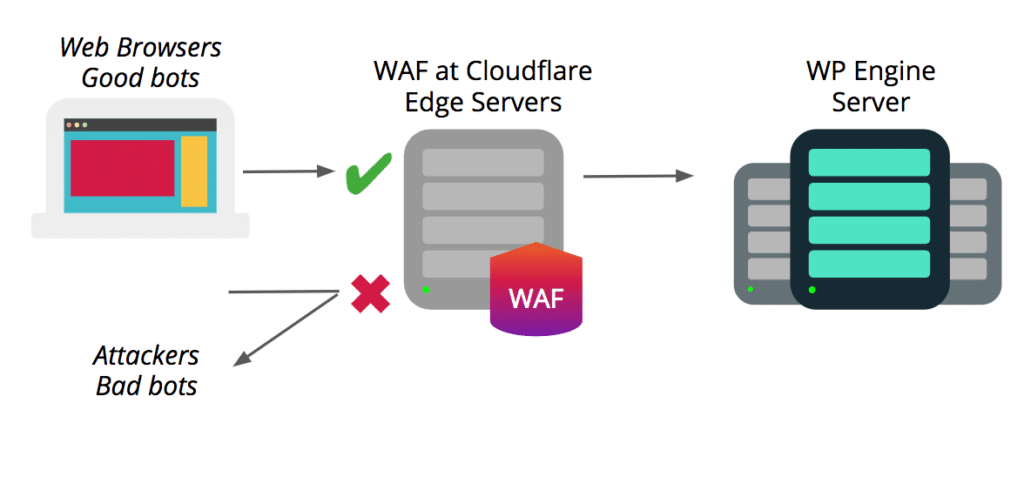
Our Enterprise-grade Web Application Firewall blocks the most common vectors for website attacks:
- Cross-Site Scripting (XSS) – These types of attacks happen an attacker injects malicious code into a legitimate (but vulnerable) application. Attackers can manipulate JavaScript and HTML to trigger the malicious code or scripts. In this way, the vulnerable application or website is used as the “vehicle” to execute the script on the end user.
- SQL Injection – SQL injection attacks happen when an attacker attempts to input meta characters into a vulnerable web-based form with malicious intent, and these attacks affect database-driven sites (which include WordPress®).1
- Cross-Site Request Forgery (CSRF) – Cross-Site Request Forgery involves taking over or impersonating a user’s browser session by hijacking the session cookie. CSRF attacks can trick users into executing malicious actions the attacker wants, or into taking unauthorized actions on the website. In this example, the session cookie is the “vehicle” an attacker uses to impersonate a legitimate user.
Cloudflare’s edge servers also use the OWASP ModSecurity rule set at the edge, protecting your website from the OWASP top-10 vulnerabilities at all times. And, the automated Browser Integrity Check will evaluate request headers to determine whether a request is coming from a real web browser or not.
In addition to the security vectors outlined above, our WAF powered by Cloudflare takes advantage of a unique set of security rules defined by Cloudflare through years of experience identifying and mitigating attacks.
Advanced DDoS Mitigation
DDoS stands for Distributed Denial of Service and is a term used to describe attacks on the Network, Transport, and Application layers of the Open Systems Interconnection (OSI) model.
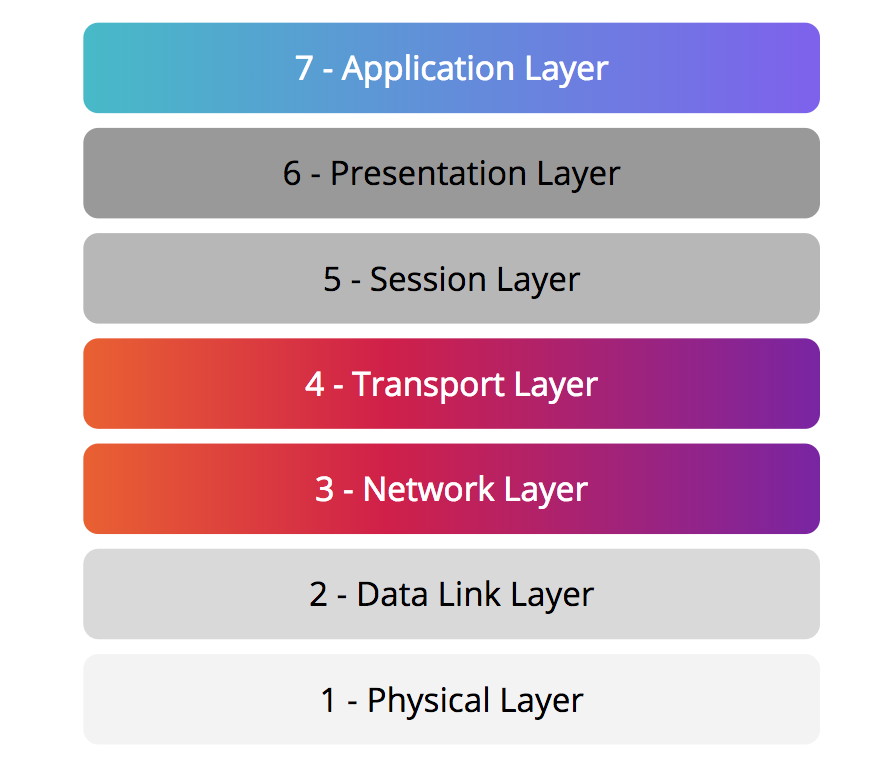
The Network Layer determines the physical path request should take through the internet (using IP and ICMP protocols), and the Transport Layer is responsible for transmitting and assembling packets of data between two endpoints (using TCP and UDP protocols). Attacks at these layers were more popular in past years and are intended to render your site inaccessible. These types of requests are automatically and silently dropped at the Cloudflare Edge network before ever reaching your WP Engine server.
Application Layer attacks have become more prevalent in recent years, and are attacks based on HTTP, SMTP, SSH, or FTP protocols. This layer is responsible for human and computer interaction, and attacks of this type specifically target an application, or website. Most often Application Layer attacks are caused by botnets, or large networks of malware-infected machines, being directed to send large requests in extreme quantities to a website with the intention of getting past security measures in order to take malicious actions. Cloudflare’s Edge servers use intuitive detection to determine whether a request for your website is legitimate, and block attacks at this level automatically. This means only legitimate traffic makes it back to the WP Engine origin server where your content is hosted.
Origin IP Protection is another way Cloudflare prevents and mitigates DDoS attacks. By nature of routing through Cloudflare’s network, the IP address of your WP Engine server is obfuscated and a Cloudflare IP address is presented instead when users inspect your website. This prevents bad actors from sending traffic directly to your origin server at WP Engine, where your web content is hosted. Instead, Cloudflare mitigates the attack in their edge network before those bad requests ever make it to WP Engine. And, unlike other DDoS protection solutions, Cloudflare provides unmetered DDoS protection–meaning they don’t cap attack size or charge overages.
Cloudflare CDN
In addition to the security measures offered by the Global Edge Security product, Cloudflare CDN adds performance and caching benefits. WP Engine’s finely tuned caching rules will also apply at the Cloudflare Edge network. This means pages can be served to users around the world faster, sending fewer requests to the WP Engine origin server.
Read more about this global network on Cloudflare. (Note: WP Engine does not currently support Mainland China zones.)
Cloudflare Polish
WP Engine enables Cloudflare Polish by default on all Global Edge Security zones. Cloudflare Polish speeds up your website by reducing image size in a few different ways: removing metadata, applying lossless file compression, and adding the WebP file format.
WebP is a next gen image format providing advanced lossless compression for images. Cloudflare Polish generates a WebP version of each image and caches it, then delivers that image to the user only if their browser supports it. According to Cloudflare “WebP lossless images are approximately 26 percent smaller than PNGs.”
The best part is, you don’t have to do or pay anything extra! Just configure GES like normal and we’ll automatically apply this huge performance enhancement to your website.
Learn more about Polish on Cloudflare’s blog.
Automatic SSL Installation
WP Engine’s Global Edge Security offering will automatically install the SSL certificates added in the WP Engine User Portal on the Cloudflare Edge servers. In this way both the connection between the end-user’s web browser and Cloudflare will be encrypted, as well as the connection between Cloudflare and WP Engine.
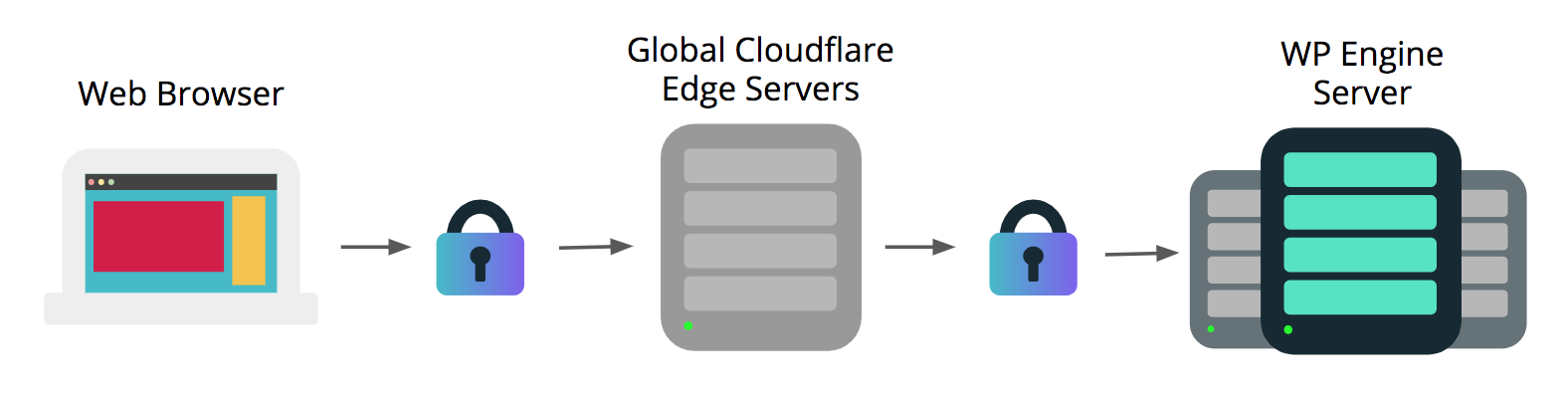
This integration means end-users will see the SSL certificate installed through WP Engine when visiting your website, rather than a shared or dedicated Cloudflare SSL certificate. The SSL integration between the Global Edge Security product and WP Engine is automatic, and ensures your website is encrypted from end-to-end.
NOTE
When pointed to Global Edge Security, SSL is automatically applied at Edge, so you will not need to add one. On GES, third-party SSL may be applied, if needed.
Limitations
Using a secondary WAF (EX: Sucuri) with GES is not recommended. Two firewall layers causes a complexity that leads to slow performance and inhibits any troubleshooting our team can assist with.
Additionally, when using the Global Edge Security product from WP Engine, your CDN, WAF, and DDoS configuration rules are automatically configured. While there is no configuration needed on your end, WP Engine cannot add special customizations to these rules for individual sites or accounts–the rulesets and configurations are fine-tuned with performance and Defense-in-Depth in mind for the protection of your websites. If your websites require a high level of customization for Cloudflare settings, or specifically need access to the Cloudflare network in China, you may want to speak to your Account Manager about other Cloudflare options instead.
Enable GES
Global Edge Security is enabled per domain from the User Portal. If the product extension has not yet been purchased, this can be done from the Products page.
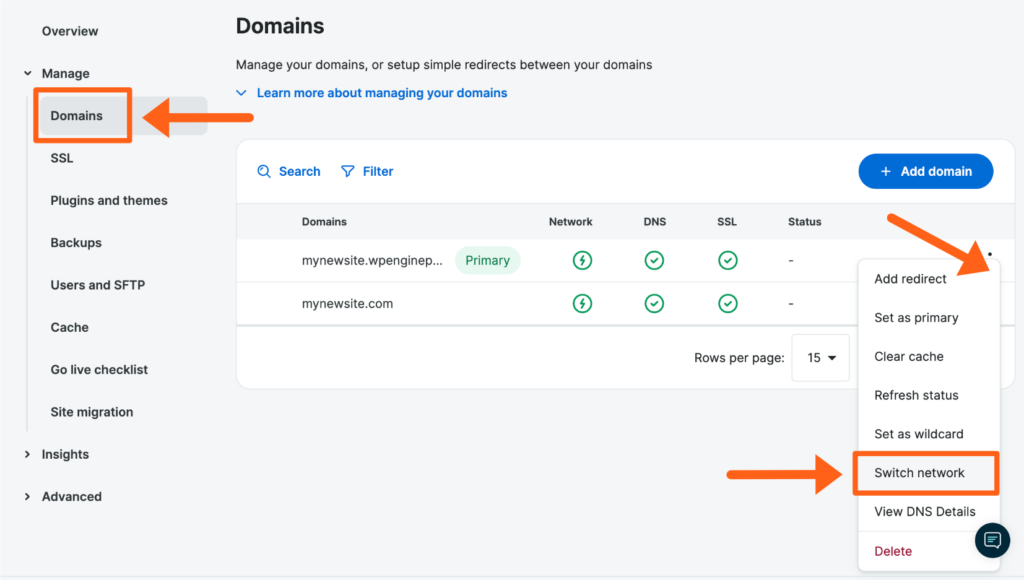
- From the Sites page, click the environment name
- Select Domains (You may have to expand the Manage dropdown section)
- Locate the domain name, and open the three dot menu icon to the right
- Select Switch Network
- Choose whether or not to include the www/non-www domain in this network switch
- Confirm that this domain will be switched to Global Edge Security
NOTE
Global Edge Security cannot be enabled for transferable environments.
Point DNS
After switching a domain to the Global Edge Security network, DNS records must be pointed to complete network activation. The Global Edge Security DNS Details will be displayed automatically when switching networks, or learn how to view DNS Details again here.
There are two options when pointing DNS:
- Point DNS to GES using CNAME flattening.
- The Global Edge Security CNAME is a unique string for each environment that includes “wpeproxy.com” (EX:
12345.wpeproxy.com). Learn how to view GES DNS details again here. - If you already have CNAME flattening configured, simply replace the current WP Engine CNAME with the new GES CNAME.
- The Global Edge Security CNAME is a unique string for each environment that includes “wpeproxy.com” (EX:
- Point DNS to GES using two A records.
- While CNAME flattening is preferred, A records are supported. To ensure maximum load balancer accessibility, two A records should be configured for any domain pointed via A record, using two separate IP addresses. Although rare, these IP addresses are subject to change for security purposes. Learn how to view GES DNS details again here.
GES Cache
By default, GES has static assets cache expiration set to 365 days. If cache expiration needs to be modified, reach out to WP Engine Support. If you’ve made changes to your site but are not seeing them reflected when using Global Edge Security, it’s very likely that the network cache needs to be purged.
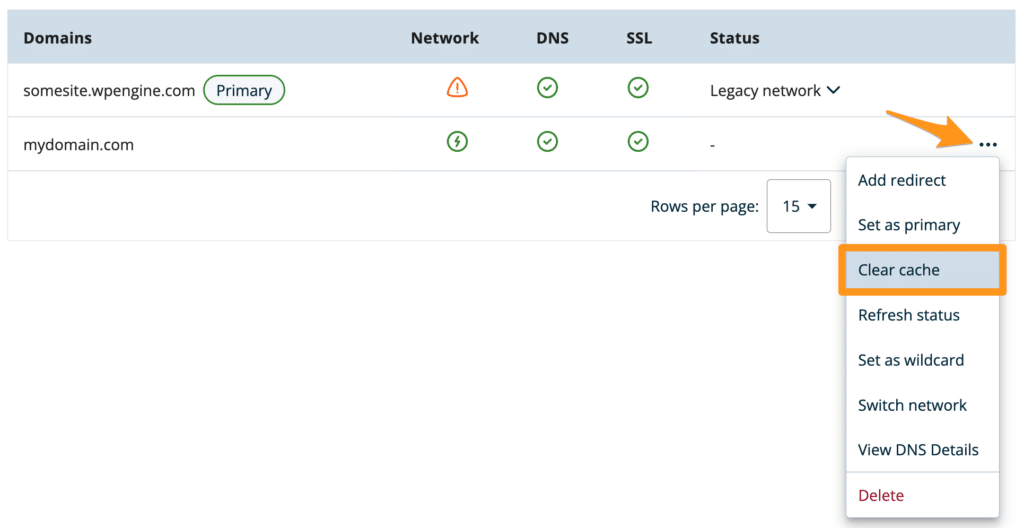
To clear domain network caches, including Global Edge Security network cache:
- From the Sites page, select the environment name
- Click Domains
- Expand the 3 dot menu icon to the right of the domain
- Select Clear cache
NOTE
Alternatively, Clear Network Caches on the Cache page of the User Portal will also clear GES caches. Learn more here.
GES Errors
If you are using WP Engine’s Global Edge Security product extension you may see new errors. Read on to learn how to interpret the error pages, and troubleshooting steps to resolve errors.
Unknown Error
This section will help you if you encounter the following error:
Web server is returning an unknown error
There is an unknown connection error between Cloudflare and the origin web server. As a result, the page cannot be displayed.
Ray ID: 1234567890-DFW
Your IP Address: 123.45.67.890
Error reference number: 520
Cloudflare Location: DFW
This error appears when there is a connection error between Cloudflare and the WP Engine origin server. While this error can mean several things, some common causes include:
- The connection was reset
- Response headers were too large (generally indicates a deeper problem with the website)
- Invalid or empty response from the WP Engine origin server
- No response headers were sent
- Presence of multiple “Content-Length” headers
The 520 Unknown Error is typically caused by something at the application layer, indicating a website-level issue rather than a server-level issue. Try visiting the site while using a hosts file trick to point your domain directly to the WP Engine IP address showing in your User Portal, and see if a different error exists which might be causing this. For more help, contact WP Engine support via 24/7 Live Chat in your User Portal.
Web Server is Down
This section will help you if you encounter the following error:
Web server is down
The web server is not returning a connection. As a result, the web page is not displaying.
Ray ID: 1234567890-DFW
Your IP Address: 123.45.67.890
Error reference number: 521
Cloudflare Location: DFW
This error occurs when the Cloudflare server received a “connection refused” response from the WP Engine origin server, or when the web server is down/restarting. If the web server is down/restarting, simply try the web page again in a few minutes.
In the case of a “connection refused” issue, usually this happens because a Cloudflare IP address has been rate-limited or denied on the WP Engine server or on the website directly through a security/firewall plugin. WP Engine allows connections from Cloudflare IP addresses, indicating the issue is most likely to be a security plugin or firewall. Check your security settings for your website, or contact WP Engine Support via 24/7 Live Chat in your User Portal for more help.
Connection Timed Out
This section will help you if you encounter the following error:
Connection timed out
The initial connection between Cloudflare's network and the origin web server timed out. As a result, the web page can not be displayed.
Ray ID: 1234567890-DFW
Your IP Address: 123.45.67.890
Error reference number: 522
Cloudflare Location: DFW
This error indicates the request timed out when trying to establish an initial connection to the WP Engine origin server. There are several conditions which could cause this error to appear:
- Your WP Engine server is overloaded with traffic, and could not respond to the connection request
- Cloudflare requests have been denied by your website via a security plugin or firewall
- Website has disabled Keep-Alive headers
- Faulty network routing
If the first or last scenario is true, try again in a few minutes to see if your request is successful, as the high traffic or routing issue may be temporary. If you continue to see this error, contact WP Engine Support via 24/7 Live Chat in your User Portal for more help troubleshooting this issue.
If the second or third scenario, check security settings for your firewall or security plugin, and ensure it is not denying Cloudflare IP addresses, or that it hasn’t disabled Keep-Alive headers, which Cloudflare requires to make connections to your WP Engine server.
Origin is Unreachable
This section will help you if you encounter the following error:
Origin is unreachable
The origin web server is not reachable.
Ray ID: 1234567890-DFW
Your IP Address: 123.45.67.890
Error reference number: 523
Cloudflare Location: DFW
This error is very rare, and typically indicates a network route to your WP Engine origin server is unavailable. This can happen if your WP Engine IP address has been null-routed, which is an extremely rare scenario. If you encounter this error, first check your DNS settings to ensure you are pointed to the correct CNAME for the Global Edge Security network. If all looks correct, please contact WP Engine Support for more help via 24/7 Live Chat in your User Portal.
A Timeout Occurred
This section will help you if you encounter the following error:
A timeout occurred
The origin web server timed out responding to the request.
Ray ID: 1234567890-DFW
Your IP Address: 123.45.67.890
Error reference number: 524
Cloudflare Location: DFW
WP Engine institutes a 60-second timeout for long-running page requests. On top of this, Cloudflare institutes a 100-second timeout of a similar nature. If a connection was established but no response was sent for over 100 seconds, this error will occur. Most often this error occurs because of long-running requests (cron jobs or imports), or because of very long database operations. We recommend batching your imports or long-running cron jobs into smaller requests so they do not exceed the timeout. If you need more help identifying the source of this issue, please contact WP Engine Support via 24/7 Live Chat in your User Portal.
SSL Handshake Failed
This section will help you if you encounter the following error:
SSL handshake failed
Cloudflare is unable to establish an SSL connection to the origin server
Ray ID: 1234567890-DFW
Your IP Address: 123.45.67.890
Error reference number: 525
Cloudflare Location: DFW
WP Engine’s Cloudflare configuration uses “Full” SSL settings, meaning it will try to connect to the WP Engine origin server with SSL encryption. This error will occur if the SSL certificate does not exist or was removed on the WP Engine origin server. If your DNS is pointed to our Legacy DNS Network, to resolve this error, simply add a free Let’s Encrypt SSL certificate for your domain in the WP Engine User Portal. If you need more help troubleshooting this error, contact WP Engine Support via 24/7 Live Chat in your User Portal.
Invalid SSL Certificate
This section will help you if you encounter the following error:
Invalid SSL certificate
The origin web server does not have a valid SSL certificate
Ray ID: 1234567890-DFW
Your IP Address: 123.45.67.890
Error reference number: 526
Cloudflare Location: DFW
This error indicates the SSL certificate on the WP Engine server is not valid. If you encounter this error, check the SSL certificate showing in your User Portal for your website. Make sure the certificate is not expired, has not been revoked, and is not self-signed. If your DNS is pointed to our Legacy DNS Network, to resolve this error you can add a free Let’s Encrypt SSL certificate from the WP Engine User Portal for your domain. If you need more help troubleshooting this error, contact WP Engine Support via 24/7 Live Chat in your User Portal.
Disable GES
To disable Global Edge Security: switch network types to the Advanced Network in the User Portal, then update DNS to point to the the Advanced Network instead. This process should be repeated for each domain where GES is enabled.
- Switch to the Advanced Network:
- From the Sites page, select the environment name where the domain has been added
- Select Domains
- Locate the domain name, and open the three dot menu icon to the right
- Select Switch Network
- Confirm that this domain will be switched to Advanced Network

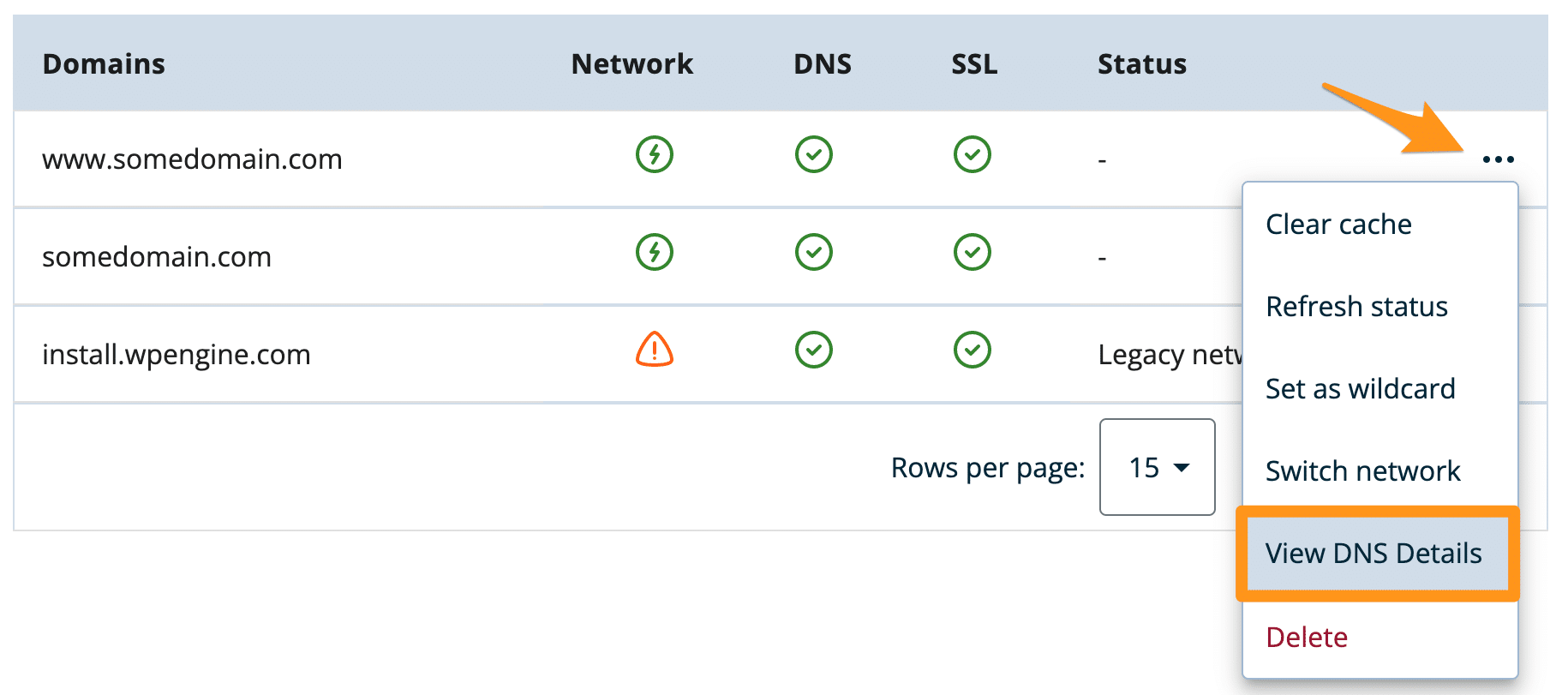
- Update DNS:
- On the Domains page, locate the domain then open the three dot menu icon to the right
- Select View DNS Details
- Use this new CNAME/IP address when updating DNS at your DNS provider
That’s it! Once DNS updates, this domain will no longer use the Global Edge Security network.
GES is enabled for each domain, be sure to repeat this process for each domain that needs GES disabled.
To learn more about the Advanced Network, and how to switch and update DNS, see the Advanced Network guide here.
NEXT STEP: Learn how to connect to SSH Gateway












